
tokens
Basic Website Development Tools Every Blockchain Developer Needs
Mon, 05/09/2022 - 21:02 — Alexis WilkeDevelopers can choose from many advanced software applications in today’s environment of intensive research on potential uses for blockchain technology. Web development tools include Ethereum DApps Development where researchers and developers strive to build decentralized apps and smart contracts. Smart contracts have the built-in ability to adjust based on changes to key terms and to monitor compliance with the terms of the contract.
Blockchain development tools help to facilitate software development. If a developer is new to blockchain or lacks experience, he or she should become ...
Protected Node Password Fork Feature
Password Fork
The new module allows for a password fork.
This means you can send your users to one specific page, and tell them about a password to use on that one page. Depending on the password, they will be sent to one of several nodes.
This works in a very similar way as the other password form, except that there is no specific destination, and the users need to know any one of the passwords.
The feature uses a specific URL defined as follow:
/protected-nodes?protected_pages=<nid1>,<nid2>,...&back=<url>
- protected_pages=<nid1>,<nid2>,...
This
Protected Node Password Field set
Once installed and properly configured, the Protected node module adds a field set in the node edit form (assuming the user has the corresponding permission: "edit any password" or "edit password <node type>".)
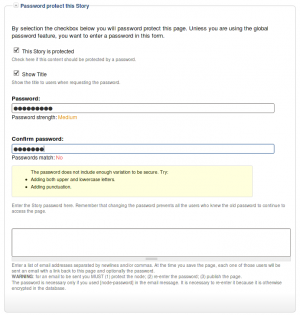 This field set includes two flags, a password, and emails (optional.)
This field set includes two flags, a password, and emails (optional.)
By default, the field set is closed unless you selected protected by default. Whether the field set should be opened or closed can selected in the node type settings.
The <node type> is protected
The first check box is used to password
Protected Node Global Settings
The protected node module has global settings found under:
Administer » Site configuration » Protected node
Protected node Statistics
The page starts with statistics to let you know how pages are protected on your website. All the counts include published and unpublished content.
- Total nodes — the total number of nodes on your website
- Unprotected nodes — number of nodes that do not have a password
-
Protected nodes — number of nodes that are current protected by a password
- Showing title — number of nodes showing their ...
To Do Tokens
The To Do module supports tokens that can be retrieved using the Token module.
The available tokens will generally appear in the list of tokens as found under a text area.
The raw tokens are no representing any security risk. They simply return the raw value instead of a more human representation of the value. For example, when the priority is "High", the raw value is 2.
To Do Rules
The To Do module includes a sub-module called To Do Rules extension.
Events
The Rules extension includes the events as follow.
Each event is sent once per user assigned to a To Do item, including self-assigned users. It includes 4 parameters: the To Do item (a node); the To Do item author; the currently logged in user; and the assigned user. The node supports additional tokens that can be used as conditions (see below).
- To Do Event Started
This event occurs when the Start button is clicked on a To Do item. This event is sent once.
- To Do Event Reminder
This event
Table of Contents Settings
Filter Configuration
At this point, most of the Table of Contents configuration is done in the Table of Contents filter.
This means multiple Input formats allow you to make use of several different configurations.
